This post will explain Free encryption software. Our current world is adjoined to an extremely high degree that even the boldest Sci-Fi authors of the past never envisioned. The Internet is, naturally, the means of this interconnectedness. And on the Internet, whatever is constructed from the info that the human users offer– even if they do not indicate to. Yes, we suggest you, particularly.
Data encryption: What is it?
Information encryption confesses meanings from numerous points of view, from the most seemingly unimportant daily angle to the most refined mathematical complexities. Let’s start with the useful aspect and say that data encryption is the best way understood up until now to protect your digital possessions and information safe from undesirable 3rd parties– that’s the something you require to understand for sure.
The encryption procedure needs two primary active ingredients: an encryption key & an algorithm. The latter processes your original information and scrambles it.
Encryption renders your information protect from cybercriminals, online dangers, and even governments. Encrypted data hence allows the interaction of large quantities of info safely through the Web.
The Ponemon Institute authored the “2019 Worldwide Encryption Trends Research Study,” which reveals that 45% of the world’s companies surveyed do use encryption in some way to protect their most delicate data. Unfortunately, the majority of the attention in the studies goes to institutional encryption. But the truth is that the tools are there for any private user to benefit from encryption technology at their will. This practice boosts personal safety online by hiding essential information from the spying eyes of malicious third parties.
When it concerns crucial data, encryption is not a high-end. It’s as vital as the data itself, whether kept in your regional hard drive or a cloud server somewhere on the planet or taking a trip in a data stream from your computer system to any designated target.
So how do you attain encryption? What are the tools general out there for you to embrace encryption as part of your standard security policies? Well, there are a lot of those tools offered for you; they are free (in fact, most of the very best encryption tools is free since it arises from open source projects and you will be able to embrace them in a heartbeat.
However before we tell you all about these tools in detail, let us give you a necessary piece of suggestions: most of the times, the encryption software will ask you to set a password as your encryption or decryption key. So always choose decisive and special passwords.
Bear in mind that if your password turns out to be “secured” or “12345,” even the best encryption protocols will not prevent a hacker from decrypting your information. Yes, it can be irritating to keep choosing a different password for every task and after that remembering or keeping track of them, however the fact is that your encryption security will be as fine as your password. This is the only possibility you have within the entire procedure to place a weak spot into the chain. Do not.
Here are some essential suggestions for producing excellent passwords:
– Each password need to be distinct and strong. Integrate using both uppercase and lowercase letters together with numbers and symbols.
– Do not pick words that you can find in a dictionary. The most timeless password hacking attack is called “dictionary” for a reason.
– Your passwords must be at least 15 characters long.
– Do not keep your passwords in a text file, your browser, or any other digital media that could end up online.
– Usage one password for one job only. Never repeat yourself in this regard.
– Do not provide your passwords away in emails, SMS messages, or other methods.
So once we have actually covered that, here’s the beef. We have a list for you that consists of a few of the world’s top free encryption programs. They will take you to a long way in protecting your digital life.
14 Best Free Encryption Software Tools In 2024
In this article, you can know about Free encryption software here are the details below;
Your own private or job-related info is out there, and it might always fall under the incorrect hands unless you do something about it. Finding a solution for it, of course, indicates taking matters into your own hands and starting securing all the information you do not desire offered to the world. In this guide, we will inform you about the very best free encryption software readily available today so that you can take a forceful position regarding your own information and security.
1. BitLocker
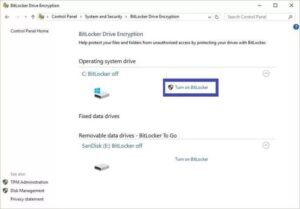
Windows BitLocker is among the most popular regional information encryption options. Lots of users prefer it. It allows you to encrypt a specific partition in your disk or disk cloning.
The BitLocker tool comes built-in in the current Windows variations (from Windows 10 on), and it also uses AES 128 and 256 bits to encrypt the partitions in questions.(AES) is the market standard for encryption algorithms, and it’s the algorithm of option in every VPN worth its salt, the military facility throughout the world, and the majority of the world’s governmental agencies.
It’s been evaluated to outrageous limits, and no group of hackers has discovered a method to split it so far– and chances are they will never overlook to do so because of the high non linearity of the transformation matrix at the core of the system. In a world like digital security, in which no guarantees are possible. AES is the you can get to having such an overall assurance.
So should you utilize BitLocker? Well, Windows is no one’s first choice when it comes to security problems or tools, however it remains the most used OS at the desktop level, so it’s ineffective to try and neglect that easy truth. So the response is yes. If you’re a Window user and you wish to execute encryption to enhance your security, Windows BitLocker is a great option, and here are a few factors for you to embrace it:
– It’s easy to use, and it’s already in your Windows OS if you’re on Windows 10 or later, so you do not need to get any extra software. You already have it, so benefit from it!
– You can use it for data breach prevention and exfiltration of delicate details out of your hard drives.
– It can encrypt your entire drive. So even if you lose the drive, no third party will be able to figure its contents out.
– Once your BitLocker Drive Encryption is activated, every brand-new file you contribute to your system gets encrypted instantly, and on the fly, no questions asked, no extra work required.
Before we give you the next advice on BitLocker, let us inform you this: this is an excellent piece of software that works well, does what it’s expected to do, and is safe and trustworthy. That being said, it stays a piece of Windows software, which has effects.
Because Windows is the Operating System with the most users in the world, windows are the best chances for any hacker to hack it. Microsoft’s dreadful history and basic practices on security problems don’t help the matter at all. As a result, most of the world’s hacking groups put a great deal of time and energy into Windows-based vulnerabilities, and they have actually done their homework with BitLocker as well. Also check top pim software
They’ve found a basic way to sniff the encryption keys if your general setup is not as protected as it needs to be. Should this be a deal-breaker for you? Not at all. However you do require to make sure that you are using secure practices and policies at every level of your Windows system. BitLocker is helpful and powerful, however it’s not magic; it requires a safe environment to stay safe itself.
2. VeraCrypt
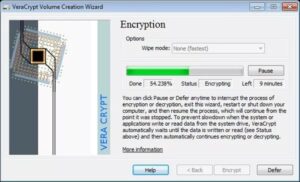
VeraCrypt is another free encryption suite offered for Windows, macOS, and, most crucially, Linux.
The software supports AES, like BitLocker. However, it also consists of two other effective encryption algorithms (TwoFish and Snake) that you can utilize in tandem with AES to have as lots of as three encryption layers on a single volume– the perfect tool for those among us who choose overkill options.
VeraCrypt is an open-source task and the primary Truecrypt alternative. That’s because it inherited the objective of TrueCrypt, a previous job of the very same time when the developing group deserted it. Its open code enables external specialists to test, audit, and take a look at the software’s ins and outs. Among the alternatives in this list, this is most likely the one that has actually made the agreement of the cryptographic community as a trustworthy tool for encryption tasks.
The project is continuously updating and keeping the software existing. The volumes it develops are uncrackable so far, and there’s every chance they will stay so even when & if quantum computers come in the industry.
VeraCrypt needs a bit of a learning for brand-new users, but it’s an easy tool to discover, and it’s one of the best choices you can have if you desire an entirely foolproof encryption technique.
3. NordVPN
Many users consider (VPN) the ultimate security service on the Internet. Sadly, this isn’t always so. VPNs are tools, like any other tool, they can be used correctly or improperly, thus attaining or beating a function.
A VPN will increase your security and privacy if it carries out 2 tasks correctly: hiding your IP and securing your traffic. Yes, Tor does that, but recall it does it only for the Tor browser. A VPN provides you those 2 services for every single little bit of traffic that is available in and out of your device.
Personal privacy is a different thing, though. Everything you do online through a virtual private network goes through the VPN’s servers. So your supplier knows whatever you’re doing. The crucial thing is: what suppliers can you rely on not to misuse that data? The ones who do not gather the stated information since they stick to a no logs policy. This is crucial. You need to comprehend that personal privacy, unlike security and privacy, is not a technological problem but a policy problem. For this reason, you need to be conscious and select your supplier appropriately.
It would be best if you constantly kept away from free VPNs. Most of them perform poorly anyhow, however that’s not the worst problem. They do not practice no log keeping. They do the opposite since their company model gathers user information they can offer to their commercial partners.
The virtual private network market has exploded in the last years so, how can you select the one you require? Well, in this manual, we will point you to our favorite VPN service provider: NordVPN.
NordVPN has a comprehensive server network. It keeps no logins, its encryption and IP masking are spotless, speeds are high enough to support 4k video streams, it can unlock almost every video streaming platform, it works out of China and other jurisdictions fond of censorship.
To keep it concise, NordVPN carries out every trick you might ever desire or get out of the very best VPNs in the industry, and it does it better than anybody else. The prices is reasonable too.
4. BCArchive
BCArchive is a free of cost folder encryption for Windows. It has an unexpected degree of versatility for a Windows tool. It lets you secure an entire folder or an individual file, depending upon your choice, with a wide variety of the very best encryption algorithms known. Those algorithms consist of Blowfish-448, Blowfish-256, Twofish, Gost, Rijndael, Snake, and Camellia-256– an outstanding menu even much better than VeraCrypt. We likewise get many hash algorithms to complete for things and a public crucial encryption method.
5. PixelCryptor

PixelCryptor is a free folder encryption folder. So what is its operating system? You thought it! It’s for Windows!
The concept in PixelCryptor’s encryption algorithm is special in the industry. It utilizes the pixels of a bitmap file. So to perform the encryption, you pick an image, and its file then becomes both an encryption secret and passwords. Decrypting the files needs the exact very same file to be readily available for the recipient.
Replacing a password and/or an encryption key for a file saves you the issue of coming up with a protected password, remembering it, interacting it securely to the other party, and all that trouble. For this reason, it’s very appealing in many methods.
The software is really friendly and easy to use. Select “Encode files” from the menu, pick the folders you want to be encrypted, click next and add the image file you will use as a pass and encryption secret. That’s it. And yes, the quality in using a nice picture as a means to communicate secret information has a gratifying element of itself.
6. LastPass

LastPass is among the most famous passwords managers on earth. Regrettably, the functions are restricted in the free choice, but it can still keep your passwords protected, along with your personal information. In addition, this piece of software will allow you to eliminate that physical notebook in which you have actually been keeping all your passwords up until now (or any other such resource you have actually used until now, and that’s naturally risky).
The user interface is easy, user-friendly, and easy to use. In extra, the technological platform includes browser extensions for Mozilla Firefox and Google Chrome and mobile apps for Android and iOS.
Upon producing your brand new LastPass account, you’ll get an offer to conserve the brand-new credentials. In addition, the tool will prompt you to establish a special password, safe and difficult to break. If several accounts utilize the very same password, it will ask you to consider using a various password.
7. FileVault 2
So you’re one of the pleased Mac campers, and you’re looking for an encryption tool that’s made to the particular taste that Apple users are known for? Look no more. FileVault 2 is specifically what you desire.
This software offers your Mac system with full-disk encryption with AES-128 encryption with a 256-bit key. We understand what you’re thinking: why is it not AES-256 instead? How come we Mac users get just half the power everyone else gets? Approved, AES-256 is more powerful than the same algorithm in its 128-bit variation. However don’t undervalue the power of (AES-128). So far, it’s passed every audit and there is no attack understood to break it so far– which’s not for lack of attempting.
There’s one catch, though. downloading it on your Mac is not as pain-free as you’re utilized to with all your software, and you will require to see and follow this guide.
8. DiskCryptor

DiskCryptor can secure your external and internal HDD, even the system partitions or ISO images, USB thumb drives, or any other storage device.
It’s an open-source Windows task that supports Twofish and Snake besides AES, like VeraCrypt.
Intuitive, simple, and effective, it will let you encrypt an entire hard disk simply by picking it and clicking “Encrypt.”. Also check Best sales management software
9. 7-Zip.
Encrypting a total partition or a whole disk is not everybody’s cup of tea. However, many users understand precisely which submits require the extra security afforded with encryption, so they prefer a tool that can do that particular task. Go into 7-Zip.
This is yet another free and open-source task understood for its simplicity, performance, and convenience.
It’s based upon AES-256 encryption, and if you’re used to software such as WinZip or WinRar, you’ll discover it very familiar currently. It does the exact same task, for the most part, but with high-level encryption included for good measure.
10. AxCrypt.
AxCrypt resembles 7-Zip in that it’s likewise an open-source project, free, and it handles encryption for specific files in a comparable way.
Premium versions are readily available for Windows, iOS, Android, and macOS.
The user interface can use AES-256 efficiently to a single file, folder or a group of files with a single right-click.
You can have your files secured for a duration or have the program decrypt them immediately once they get to their location.
11.Tor Web browser.

Extremely couple of tools effectively guarantee personal privacy, anonymity, and security online than the Tor internet browser. It gives you confidential access to the web and secures all your traffic. It also hides your IP address by obstructing some popular plugins (Flash, RealPlayer, Quicktime) that can give your IP address away.
The Tor Browser is essentially a variation of Mozilla Firefox modified to link to the Tor network. The network supplies IP masking and encryption, so the prey website you arrive has no thought about where you’re, and no third party can find out your activities. If you select to adopt this internet browser, you require to understand that you should not mess around with it. Do not include any plugins or extensions to your Tor Browser because they could beat the purpose of using Tor browser in the first place.
Tor is likewise the door to dark website. We’re not saying that it’s something you need to have an interest in, however it’s one of Tor’s specifying functions as it’s the only method to see.onion web pages.
When you want to conceal your IP and have your traffic encrypted, Tor is the very best choice by far. But you must be aware of a number of things. First, the security Tor offers you uses only to the web browsing you carry out utilizing the Tor browser. Everything else you see or do on the Internet remains revealed.2nd, Tor will route your traffic through at least 3 nodes in the Tor network whenever you ask to reach an URL. Each node secures and decrypts the data, and the servers can be rather far from each other. The outcome is that Tor surfing is extremely slow. If you’re seeking to use this tool for greatly graphic sites or to see streams, you’re trying a spoon on a steak.
12. HTTPS Everywhere.

Securing your regional files or partitions is a great security policy for sure. But it’s insufficient. Communications are at the heart of the Web, so you require to ensure that your communications are not offering your game away to cybercriminals.
In this case we are saying about the most common and vital internet operation: web browsing. There are insecure and safe and secure ways to browse the web, and you require to choose the safe choice always. And that’s what it can do for you.
HTTPS Everywhere is an internet browser extension available for Google Chrome, Firefox & Opera. It guarantees that all your web traffic is encrypted at everytime so that no digital eavesdropper can track your activity.
13. Silver Secret.
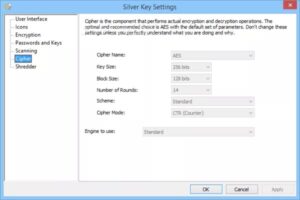
Silver Key is also a Windows based free encryption software. This one has the more specific objective of creating an encrypted package that you can send over the Internet without worry of interception. It can even self extract if you can supply the proper password for an offered package. So the user does not need to have actually Silver Key set up to decrypt the details you send them. The cryptographic algorithm is (AES 256).which is the market requirement for cryptography, VPNs, and every job that needs the best encryption available.
This deceptively user friendly program includes numerous appealing features such as shredding the files after encryption, including a private message, adding an openly noticeable description, and many more.
There are a lot of excellent free encryption tools for Windows, as it’s the case with almost every software classification. However, Silver Key sticks out from all of them due to the fact that it’s convenient to utilize.
14. Sophos Free Encryption.
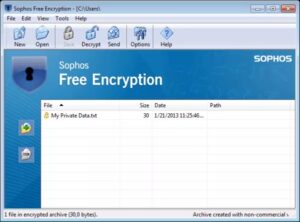
Again, a Windows folder encryptor. This one provides you the extra alternative to compress your folder, conserve a little bit of area in your storage devices, and make the information transport procedure quicker.
Sophos Free Encryption also offers you the capability to create a self-extracting encrypted archive (like Silver Secret), which increases the effectiveness of the encrypted parcels because the recipient needs no extra software to draw out the “plain text” contents. In addition, there’s a friendly password manager consisted of so that you can conserve and keep track of the pass you use for every private encrypted plan.
Online security procedures you should consider adopting.
As specified earlier, encryption is an exceptional security procedure, however it’s no silver bullet. Keeping yourself digitally safe needs an integrated method that includes extra procedures to encryption.
These are one of the most basic security steps you must practice at all times:.
– Keep your operating system and other pertinent software updated with the most recent security patches at all times.
– Choose an excellent antivirus suite and utilize it consistently. Yes, the very best ones require spending for a license or a subscription. However think about this as a financial investment.
– Understand how hazardous public WiFi hotspots can be. Yes, all of us like searching around the web on our phones, tablets, and laptop computers while we drink our favorite coffee at Starbucks. Hackers enjoy that too. These WiFi or hotspots are not secured by encryption of any kind, so every usage is freely relaying whatever they do to the world at large. The best thing to do about these sort of environments is to prevent them altogether. If you absolutely should utilize one of these (on vacation, for instance), then you absolutely need to utilize these WiFi sites with a VPN. Anything except that renders you hopelessly vulnerable.
– Inform yourself. Keep checking out the articles you can find on this site, perhaps buy a book. You require to be knowledgeable about digital security since you can’t intend to have a 100% offline life in this day. Continued education on this subject is essential because it alters rapidly, and yesterday’s news is useless today.
Why do I require encryption software right here and now?
Data breaches are the support these days’s hyper-connected world. That, of course, leaves much to be preferred, particularly if your information gets breached and your security becomes threatened. Nevertheless, your safety is in your own hands. You have every chance to be fierce and prevent any crook from utilizing your own data against you.
And how do you accomplish the top security possible in your own digital life? Well, that takes a nice approach to safety. You need to inform yourself about the tools and resources around you, embrace the correct security practices, and find out how to use a minimum of the necessary tools, such as a VPN, Tor, VeraCrypt, and others. Free encryption tools are one component in this salad. They are absolute.
Let us be clear about something. encryption tools alone will not provide you the complete answer. This is no silver bullet at all. Nevertheless, they are a vital part of any successful security policy. While encryption software can never be the entire service, the reality is that any great option always includes encryption software.
Over the last couple of years, the brand-new big thing in Web innovation has been cloud storage. Google Drive OneDrive and similar services are all the rage now, and having an account with them has actually become as necessary as having an email address. Subsequently, too many users publish personal files to their cloud storage without believing too much about it and, sometimes, leaving them visible. Also check best inventory management software
There’s absolutely nothing incorrect with cloud storage. It’s practical and important; it conserves you a lot of inconvenience and carries around those frustrating USB sticks. But it can be utterly dangerous. And how do you resolve this security problem? Well, this is one of the cases in which one free encryption tool can supply you with the total service to your problem.
Conclusion
Being safe online is not a luxury. It’s a necessity. The digital way of life is a brand-new function in the human experience. It’s become really extensive really rapidly in the last couple of years. Consequently, most of us do not understand how to deal with it properly because it’s absolutely nothing we could have gained from our grandparents.
But however brand-new this thing is, or however easy to understand it can be for any of us to be uneducated at it, the truth remains that if we get our identity stolen online, our important working data erased or corrupted, or the personal information shared out outdoors, we will discover ourselves in a world of problem and pain.
As things stand, if you’re going to utilize a computer in the house or your work, a tphone, or a tab, then you need to learn a minimum of the fundamentals about digital security as quick as you can.
Security is an perspective, not a recipe. It’s not just about doing two or three things correctly but about understanding the whole picture.
Encryption is one of the crucial elements in any good security practice (possibly it’s the most crucial consider technological terms). So it is essential to know that it’s available to you as a private user. In addition, there are plenty of exceptional software options out there that will allow you to practice encryption with the same degree as the CIA does.
We hope that you’ll discover the time to browse and download a few of the encryption tools we’ve presented you in this guide, have fun with them a little, and decide to embrace as many of them as your digital way of life warrants. Encryption has a credibility as a geeky toy, something quite complex that only the most sophisticated users can master. Nevertheless, we hope we have shown you that the tools in this short article will make your encryption experience pain-free, basic, and straightforward since there’s one thing you need to focus on past anything else when you are online to stay safe and have privacy!